

Consider a chemical refinery or a power plant operating like clockwork; all processes are controlled and monitored, all safety measures are being initiated, and all the systems are being linked together safely. The result? No unplanned downtime, smooth operations, and complete confidence in the safety of assets and people.
Now think of a facility with no rules or regulations. Any wrong setting or unauthorized access might result in failure of equipment, accidents, or even wide-scale power shutdowns.
This is what happens in OT environments when cybersecurity standards are disregarded. The absence of explicit structures to address the risks, segment networks, and attain control mechanisms puts the infrastructure at the risk of cyberattacks that can stop production and place whole communities at risk.
This is where OT cybersecurity standards step in. These standards, much like traffic laws on a busy highway, offer organized international standards to enable industries to secure their systems, data, and individuals. They are the foundation of industrial cybersecurity, as well as operational resilience.
In this blog, we’ll explore what OT cybersecurity standards are, major challenges faced by industries in their compliance, and practical steps in implementing industry relevant standards into your facility.
What Are OT Cybersecurity Standards?
OT cybersecurity standards define how industries can safeguard their control systems, networks, and essential operations to cyber threats and system breakdowns. They introduce order, predictability, and discipline in the workplaces where safety and continued operation are not optional.
At their core, these standards establish definite guidelines on how to handle risks, control access, network segmentation, data flow security, and cyber incident response. They make sure that all elements of an industrial process, such as sensors and PLCs, SCADA systems, and remote access points, are safe and compatible.
Even a minor security breach can lead to halting production, damaging equipment, or mass shutdown of operations in an industrial environment. OT cybersecurity standards serve to prevent such occurrences by integrating security into day-to-day activities, rather than viewing it as an adjunct component, but instead, as a component of system design and sustenance.
These standards serve as a guide on safety, whether in energy plants, refineries, or manufacturing sites, acting as a kind of navigation system, enabling operators to take the correct security decisions, be resilient and continue doing business in a threat environment that is constantly changing.
Why Do Industries Need Standards?
Modern industries are deeply connected. A power plant in Texas might rely on software from Europe, while a petrochemical facility in Saudi Arabia could be using components built in Asia. This global chain creates opportunities but also vulnerability.
Hackers don’t stop at borders. They look for weak points. Standards bring consistency. That way, whether you’re running a gas pipeline in the U.S. or a desalination plant in Jeddah, you’re following trusted, tested rules.
OT Cybersecurity Standards You Need to Know
Not all standards are built the same. Some apply across the globe; some are tied to specific regions, and others are created for certain industries.
Global Standards
- IEC 62443
Focus:
It is the go-to cybersecurity standard designed for industrial environments.
What it covers:
It provides clear measures to be taken in securing SCADA systems, control networks, and automation equipment. This standard takes organizations through access management, network segmentation, and securing systems on all levels, including the individual equipment and entire industrial systems. It is flexible and used across many industry sectors including oil, gas, and energy sectors.
Why it matters:
Industrial systems can’t afford downtime or safety risks. This standard helps make sure that even if one part of your network is attacked, the rest stay protected. It gives structure to how you design, operate, and maintain secure industrial control systems, keeping both production and people safe.
- International Society of Automation (ISA)
Focus:
ISA doesn’t just write standards; it empowers people to apply them.
What it covers:
As one of the main contributors to IEC 62443, ISA provides the bridge between theory and practice. It provides career development, practical training, and certification of engineers, operators, and cybersecurity experts to better implement the theory into practice.
Why it matters:
It is one thing to have a standard but to know how to use it effectively is another thing. ISA also makes certain that the teams are equipped with practical expertise to implement the best practices of cybersecurity with confidence and consistency in the industrial setting.
- ISO/IEC 27001
Focus:
ISO/IEC 27001 is the global standard for managing information security not just in IT, but across the entire organization.
What it covers:
It assists businesses in setting up a well-structured Information Security Management System (ISMS). This involves risk evaluation, articulate cybersecurity guidelines, frequent audits, and defined roles to all involved.
Why it matters:
Cybersecurity isn’t a one-time project; it’s a process. ISO/IEC 27001 keeps organizations continuously improving by making security part of daily operations. It helps industries move from reactive protection to proactive defense, creating a strong, security-aware culture across all levels.
United States
- NERC CIP
Focus:
NERC CIP (Critical Infrastructure Protection) sets strict rules for keeping the electric grid secure across North America.
What it covers:
It defines how utilities must protect their critical assets from power generation to transmission systems. The standard includes detailed requirements for access control, incident response, recovery planning, and ongoing monitoring.
Why it matters:
When it comes to electricity, there’s no room for error. A single weak point can trigger a chain reaction and cause massive blackouts. That’s why NERC CIP compliance is mandatory, not optional. It ensures the reliability and safety of the entire energy network of millions depend on every day.
- NIST Cybersecurity Guidance (including NIST 800-82)
Focus:
The NIST framework provides practical guidance for securing critical infrastructure, especially where IT and OT meet.
What it covers:
It adapts traditional IT cybersecurity practices for industrial environments like power plants, chemical facilities, and manufacturing sites. NIST SP 800-82, in particular, focuses on how to protect Industrial Control Systems (ICS) while maintaining uptime and operational safety.
Why it matters:
Industrial operations can’t just “pause” for a security update. NIST helps organizations strengthen their defenses without disrupting production. It balances safety, reliability, and security so industries can stay both operational and protected.
- Cybersecurity Capability Maturity Model (C2M2)
Focus:
The Cybersecurity Capability Maturity Model (C2M2) helps organizations assess and improve their cybersecurity posture step by step.
What it covers:
Developed by the U.S. Department of Energy, C2M2 provides a structured framework to measure where an organization stands from basic awareness to advanced protection. It helps map out gaps, set priorities, and plan long-term improvements. Many utilities and energy companies use it as a performance benchmark.
Why it matters:
Cybersecurity is a journey, not a one-time achievement. C2M2 gives organizations a clear roadmap to grow stronger over time, helping them focus on resources where they matter most and continuously raise their defense levels.
- Cybersecurity and Infrastructure Security Agency (CISA)
Focus:
CISA doesn’t issue standards. It empowers organizations with tools, resources, and intelligence to stay ahead of threats.
What it covers:
It provides playbooks, alerts, and best practices to help industries handle incidents, protect assets, and share real-time threat information. CISA also issues specialized guidance for OT environments, such as vulnerability advisories and response frameworks.
Why it matters:
Cyber threats evolve fast, and no single standard can cover it all. CISA acts as a real-time support system helping industries prepare, respond, and recover faster. It turns lessons from real-world incidents into actionable guidance that keeps organizations one step ahead.
Saudi Arabia & Middle East
- National Cybersecurity Authority (NCA) Controls
In Saudi Arabia, NCA sets mandatory rules for sectors like energy, finance, and government services. These are part of the Kingdom’s national security strategy and are non-negotiable for operators (NCA, 2022). - High Commission for Industrial Security (HCIS)
HCIS focuses on both physical and cyber protection for facilities such as oil, gas, and chemical plants. No major industrial project in Saudi Arabia can proceed without meeting HCIS requirements. - SABIC X01-E02
SABIC enforces its own cybersecurity program to safeguard petrochemical production. These rules align with IEC 62443 but are tailored to Saudi Arabia’s chemical industry. - Saudi Aramco SACS-002 (Cybersecurity Compliance Certificate Program)
Aramco requires all industrial facilities under its umbrella to meet strict cybersecurity controls. These rules ensure safe operations in one of the world’s most critical oil ecosystems.
4 Major Challenges in Compliance
- Overlapping Standards Create Confusion
Many industries operate under different rulebooks at the same time. This overlap makes them confused in the matter of which requirement comes first. With this confusion and unclear alignment, there’s a risk of wasting time and duplicating efforts.
- Lack of Skilled Professionals
OT cybersecurity is highly specialized. IT teams understand networks while engineers understand processes, but very rarely master both. This gap could make it harder to interpret and apply complex standards when necessary.
- High Costs for Smaller Operators
Compliance programs cost large organizations millions, and small operators cannot afford the programs because of the small budgets. The cost of equipment, audits and training may seem daunting, but the danger associated with non-compliance is even more severe.
- Constantly Evolving Threats and Standards
Cyber threats do not just stand still, nor do the standards designed to prevent them. What was acceptable two years ago can be obsolete today. It takes daily effort and resources to keep up with revisions.
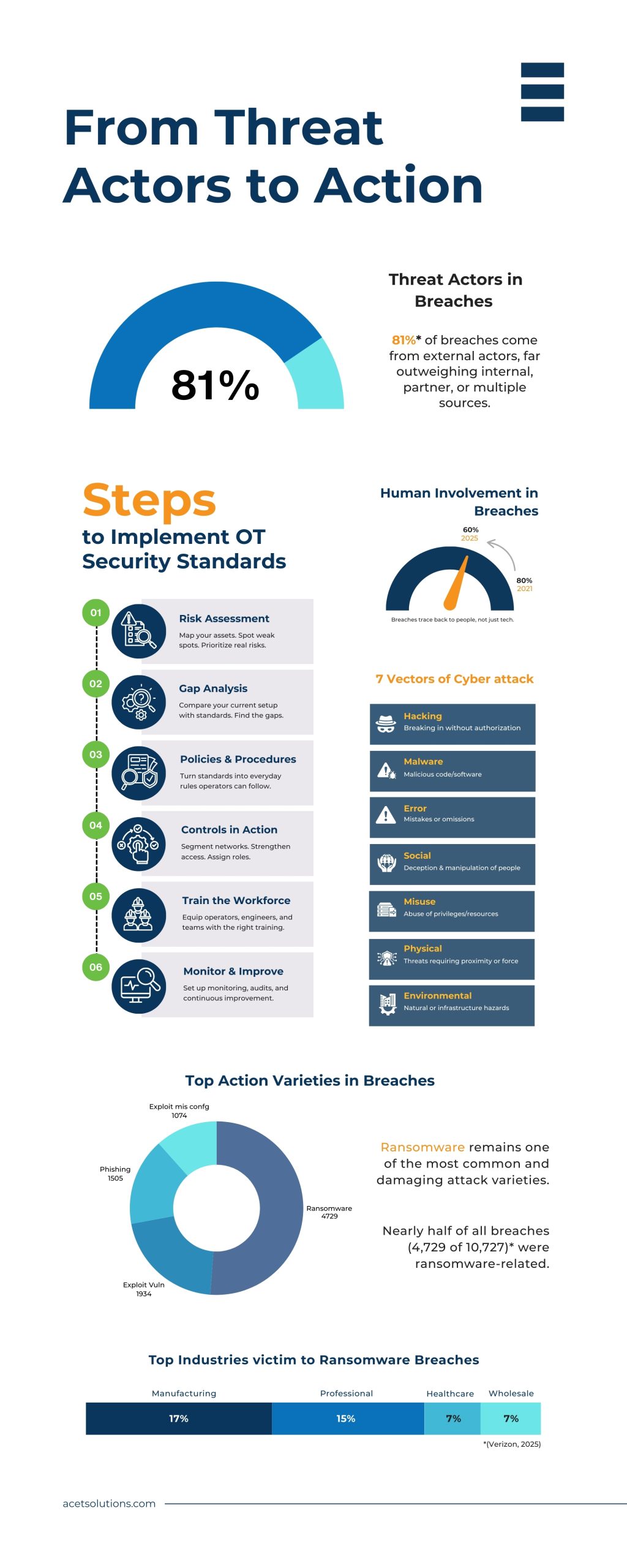
How to Implement OT Security Standards in 6 Practical Steps
Implementing OT standards isn’t just about compliance; it’s about building resilience into daily operations. Here’s a clear roadmap industry that can follow to put them into practice.
- Assess Your Risks
There are different vulnerabilities in different industries. The first step is to map out your assets and ask yourself the question of what the risks are if we get hit today. This gives you an idea to help prioritize where more effort is needed.
- Identify the Gaps
Look through what the standard expects from you and then compare it to your current setup. This will help identify gaps in your setup. It could be weak response plans, poor network segmentation, or outdated firewalls, etc.
- Establish Policies and Procedures
Standards can only be implemented practically if they can be applied to daily operations. For that purpose, turning them into practical rules and policies that can be used by engineers and operators is more useful.
- Implement Technical and Organizational Controls
After making the policies, they need to be put into action. This could be by segmenting tools, tightening access, or deploying monitor tools. With this intact, it’s equally important to assign roles, so everyone knows their responsibilities.
- Train and Empower the Workforce
Even the best controls would be fruitless if people didn’t know how to use them. Right drills and training for engineers and security teams should be done regularly and practically.
- Monitor, Audit, and Improve Continuously
Complying with standards is not enough. You need to continuously monitor them by setting up systems and running regular audits. Cybersecurity is an ongoing threat. The defenses must evolve with threats.
Benefits of Implementing OT Cybersecurity Standards
- Stronger protection against cyberattacks
OT cybersecurity standards offer a methodical way of detecting and remedying vulnerabilities before they are exploited by attackers. They advise industries on how they can protect networks, regulate access, and secure sensitive systems that operate essential operations. Adhering to these models, organizations decrease the risks of data breaches, system hijacks, or physical interference because of cyber-attacks. In short, standards turn security from a reaction into a well-planned defense. - More reliable operations
With security controls and adequate system maintenance, industrial operations become more predictable and stable. OT standards encourage proactive maintenance, risk evaluation, and real-time monitoring, which minimize unexpected interruptions and operational mistakes. This ensures that production lines are maintained in a smooth operation besides the safety of workers, equipment, and the environment. Trustworthy systems imply more productivity and cost reduction in the long run. - Greater trust from stakeholders
Adherence to the accepted standards of cybersecurity sends a strong message to investors, regulators and clients that the organization cares about security, transparency and sustainability. The stakeholders are assured that the company operates following the best practices globally and capable of securing their operations even in the event of a crisis. - Future readiness
Threats and technologies are changing at an extremely fast rate, and so are the standards that regulate such. Companies that adhere to OT cybersecurity models are more likely to respond to emerging technologies such as IoT, AI, and industrial systems based on the cloud. These standards provide a culture of constant improvement so that the companies are not merely responding to changes, but they are ahead of them. Compliance today builds resilience for tomorrow.
Conclusion
OT cybersecurity standards are no longer a choice to make, but the basis of safe, reliable, and future-proof industrial activities. Power plants, oil refineries, factories and utilities upon which millions depend daily cannot spare to treat them like a checkbox exercise.
Industries are not just ticking compliance boxes when they implement global, regional, and sector-related standards. They are fortifying themselves, cutting down time, and gaining confidence in regulators, partners, and the people.
The actual benefit lies in the fact that these standards must be integrated into day-to-day operations at least so that they are not merely on paper. It is those companies that act now, which will be in a position to contend with the rising tide of cyber-related risks in the year 2025 and beyond.
Learn how ACET Solutions help organizations across industries achieve compliance, enhance resilience, and build safer connected operations.
Visit our OT Cybersecurity Services.
Frequently Asked Questions (FAQs)
They are rulebooks created by global bodies, governments, or industries to guide how companies should protect their operational technology systems, like power grids, oil rigs, or factories.
No. Some standards apply globally, but many are regional or industry specific. For example, NERC CIP is for the North American power grid, while HCIS is required for Saudi oil and gas.
Some standards, like ISO/IEC 27001, are voluntary but widely adopted. Others, like NERC CIP or HCIS, are legally enforced, and non-compliance can mean heavy penalties.
It takes effort, but it’s manageable if done step by step starting with risk assessments, closing gaps, and then building policies, training staff, and monitoring continuously.
Because the cost of non-compliance downtime, cyberattacks, lost trust is far greater. Standards not only reduce risks but also improve reliability and business reputation.
Related Articles






