
In Operational Technology (OT) environments, where systems such as SCADA, PLCs, DCS, and safety instrumentation control critical infrastructure, cybersecurity isn’t just about tools; it’s about strategic governance. A common misconception is mixing asset discovery with asset management. While both are essential, they serve fundamentally different roles in securing OT systems. One is reactive, the other strategic.
In an OT Cybersecurity webinar series, Mubarik Mustafa, Principal Consultant for OT/ICS cybersecurity at ACET Solutions, provided critical insights into the relationship between asset discovery and asset management within OT, emphasizing the need for robust asset management practices for effective cybersecurity.
Watch the full OT Cyber Security webinar here.
In this article, we will go into detail and explain the core differences between asset management and asset discovery.
OT systems are the backbone of industrial facilities, from refineries to power plants. Unlike IT, these environments prioritize safety, availability, and operational integrity. Here, uncontrolled changes can lead to catastrophic failures. This is why Management of Change (MOC) is essential to ensure the continuity of operations without disruption. Even a small change, like swapping a pressure transmitter, follows a comprehensive validated process:
Mubarik Mustafa said, “In OT, you never make a change first and document it later. That’s a recipe for chaos.”
Yet when it comes to cybersecurity, many organizations bypass this core principle and rely solely on asset discovery tools that react to changes, instead of enforcing asset management processes that control them.
Asset Discovery tools scan OT networks to identify devices (IPs, models, firmware, etc.) and generate real-time inventories. They excel at:
While the detection capabilities of these systems are valuable, they do come with limitations, as they are reactive by design and detect changes after they occur (e.g., a new device joins the network). Sometimes it offers incomplete, inaccurate, or limited visibility due to the diverse nature of OT devices and inaccessible networks, field instruments, or segregated networks, as well as little to no insight into offline devices. In addition, it offers no control, and discovery can’t prevent unauthorized changes, as it only reports them.
“Asset discovery gives you information after the change has happened. In OT, that’s too late,” said Mubarik.
Asset Management: Proactive Governance for OT Security
True OT resilience requires Asset Management—a framework aligned with industrial MOC principles and mandated by international cybersecurity standards (e.g., ISA/IEC 62443, NIST, NERC). This involves:
“Asset discovery is not a replacement for asset management. You need both, but management must drive the process.” Mubarik Mustafa
If a network scan detects an unauthorized device, Asset Management processes determine:
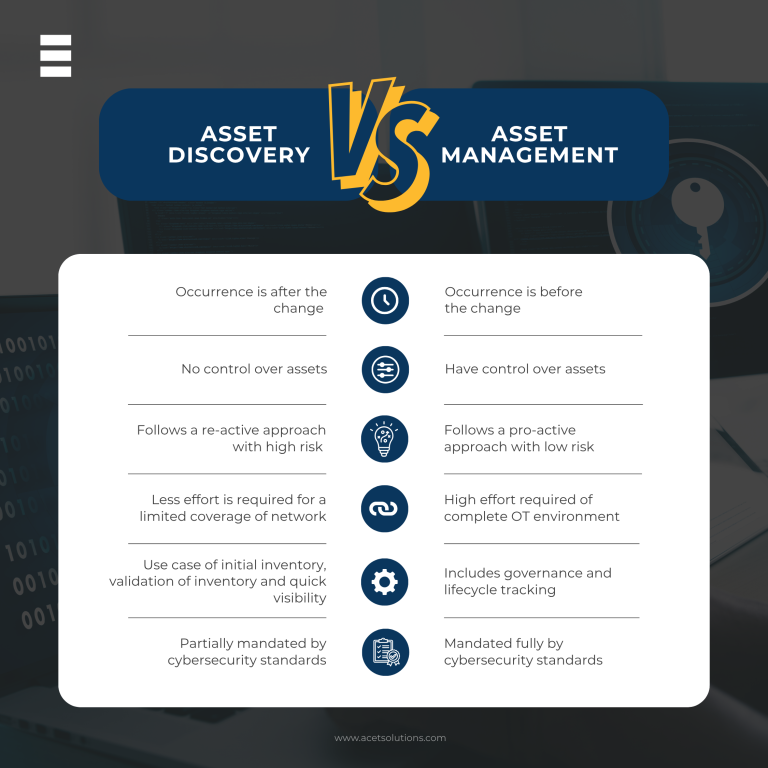
OT environments demand proactive control, not just visibility. While asset discovery provides quick visibility and helps in building an initial inventory – an “as-is” picture after changes have occurred – of your OT assets, and can serve as a valuable tool for validating your master asset management database. However, it cannot be considered a replacement for asset management.
True Asset Management in the OT environment involves following a Management of Change (MOC) process, which includes design, documentation, approval, and implementation within the “as-built” documentation to reflect the current state before a change is made. This proactive approach mitigates significant risks associated with health, safety, environment, and operations.
To learn more about how ACET Solutions can help you with robust OT assessment and management strategies, visit here.
Related Articles
© 2025 ACET Solutions . All Right Reserved.